Many online game players have had their accounts stolen. If they search on GOOGLE, there are about 486,000 search results that match the "World of Warcraft account stolen". No wonder an ashes player of "World of Warcraft" said, "You haven't played this game without being stolen!"
According to the statistics of the "Chinese Game Industry Report 2007", the number of online game users in China reached 40.17 million in 2007, the actual sales revenue of the online game market reached 10.57 billion yuan, and the online game virtual goods transaction market scale was 3.78 billion yuan. It is estimated that by 2012, the market size of virtual goods transactions will grow to 19.68 billion yuan, with a compound growth rate of up to 39.3%. While the online game market is unprecedentedly prosperous, the report also pointed out that economic crimes against virtual goods, due to the lack of laws, cause difficult sentencing and punishing is not strong. Potential crisis.
If it is an ordinary player's account, the loss of stolen may not be great. However, some high-value game account may be sold for a high price of hundreds of thousands of yuan. Driven by financial interests, some well-known accounts have become targets of Trojan virus attacks. They used spoofing, camouflage, and other methods to track and crack accounts by means of web page hanging horses and attacking system vulnerabilities. For example, the account of Monster Killed, the champion of the "World of Warcraft" Arena National Challenge, was unfortunately stolen in May this year.
So, what technologies can replace the traditional static password (user name + password), effectively prevent account theft, thereby protecting the interests of players? Compared with biometrics such as dynamic passwords and fingerprints, online identification based on USB Key is more convenient and safe.
At present, the identification of most online game players is still only verified by the user name and password. All of this information may be intercepted by the Trojan horse when input. The user name and password information can also be found in the history of the web page. As long as anyone knows the user name and password of the player, he can operate his account and buy and sell his virtual assets. If a USB Key is used, the identification based on the encryption algorithm will be performed when players log in and buy and sell equipment. The USB Key uses a random "question-response" mechanism. The authentication information code (MAC) required by the network server cannot be simulated by the Trojan horse, so it cannot pass the legal identity authentication and cannot log on to the network server.
The random "question-response" mechanism is shown in Figure 1. The USB Key uses the random "challenge-response" mechanism to authenticate the identity of the online game player by the network server. The USB Key has built-in encryption algorithms such as MD5 (Message Digest Algorithm 5) or SHA-1 (Secure Hash Algorithm 1), and a key to prove the identity of the user is stored in the USB Key and the network server in advance. When logging in, the user first sends a verification request to the network server. After receiving the request, the server generates a random number and sends it back to the USB Key inserted in the user's PC, which is called "challenge". The USB Key uses the random number and the key stored in the USB Key to perform an encryption operation, and the resulting MAC is transmitted to the server as authentication evidence, which is called a “responseâ€. At the same time, the network server uses the random number and the customer key stored in the database to perform an encryption operation. If the operation result is the same as the response result returned by the user, the user is considered legitimate.

Figure 1 Random "challenge-response" mechanism authentication process
With this mechanism, since the key that can prove the user's identity is neither transmitted on the network nor appears in the memory of the client computer, neither the hacker on the network nor the Trojan program in the user's PC can obtain the key. In addition, since the random number used in each authentication process and the operation result MAC are also different, so even if these data are intercepted during the network transmission process, there is no value for reuse.
However, is it possible to use this data to reverse the user's key? In the process of identity recognition, the encryption algorithms used are irreversible operations, that is, the implicit password cannot be derived from the random number and MAC. This fundamentally guarantees the security of online identification.
MD5 and SHA-1 algorithms
MD5 and SHA-1 are currently the most widely used single-hash function encryption algorithms. The structure and strength of these two algorithms have many similarities.
As shown in Figure 2, taking the SHA-1 algorithm as an example, its input data has a total of 512 bits, including a 64-bit password and a total of 448 bits of input information (consisting of variables, random numbers, and constants). The SHA-1 algorithm consists of 32-bit addition, logical operation, and cyclic shift. After looping 80 times, the MAC of the operation result is 160 bits.

Figure 2 SHA-1 algorithm calculation model
In addition to irreversibility, the SHA-1 algorithm has the following two characteristics.
â— Anti-collision: For a specific MAC, it is difficult to find two different input information.
â— High avalanche effect: Any change in the input will cause a huge change in the MAC.
The biggest difference between the MD5 algorithm and the SHA-1 algorithm is that its MAC is 128 bits and the number of loops is 64. Relatively speaking, SHA-1 is stronger against forcible attacks, while MD5 runs faster, and these two algorithms can be flexibly selected according to different levels of information security requirements.
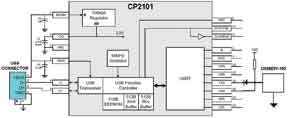
Figure 3 USB Key structure diagram based on SHA-1 algorithm
USB Key based on encryption algorithm
If you want to achieve higher security, you can design a USB Key that uses the SHA-1 algorithm for online game player identification. Figure 3 is an example of a USB Key circuit designed based on the SHA-1 algorithm. CP2101 is a single-chip bridge from USB to UART. DS28E01-100 is Maxim's SHA-1 device. It has a built-in 512-bit SHA-1 engine and 1024-bit SHA-1 protected EEPROM memory. Each SHA-1 device has a unique 64-bit ROM ID, making it possible for each device to load a unique password, and the security of the system does not depend on a single device.
These Otg Usb Flash Drive are compatible with all Smart phones that have a Micro USB port. Such as Samsung, HTC, Nokia, Sony, Google, Huawei and other smart phones.

These OTG Usb Flash Drive are also compatible with all Iphoness that have a Micro USB port. Such as iPhone, iPhone 3G, iPhone 3GS, iPhone 4, iPhone 4S, iPhone 5, iPhone 5C, iPhone 5S, iPhone 6, iPhone 6 Plus, Usb Flash Drive for Ipad including iPad, iPad 2, iPad 3, iPad 4, iPad air, iPad mini, iPad mini 2, iPad mini 3, iPad mini 4 and more.


We are a professional Chinese manufacturer of OTG USB Flash Drive , and look forward to your cooperation!
OTG Usb Flash Drive
Otg Usb Flash Drive,8Gb Otg Phone Usb Flash Drive,Otg Multifunctional Usb Flash Drive For Iphone ,Otg Mini Usb Flash Drive For Ipad
Reteck Storage Device Co., Ltd. , https://www.reteck.com