The RSA public key encryption algorithm was proposed in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman. It was first announced in the United States in July 1987, when three of them were working internships at the Massachusetts Institute of Technology. The RSA is composed of the letters of the three names of the three of them.
RSA is currently the most influential and most commonly used public key encryption algorithm. It is resistant to most of the password attacks known to date and has been recommended by ISO as the public key data encryption standard.
Today only a short RSA key can be broken by a powerful method. As of 2008, there is no reliable way to attack the RSA algorithm in the world. As long as the length of the key is long enough, the information encrypted with RSA cannot actually be broken. But today, with the growing maturity of distributed computing and quantum computer theory, RSA encryption security has been challenged and questioned.
The RSA algorithm is based on a very simple theory of number theory: it is very easy to multiply two large prime numbers, but it is extremely difficult to factorize the product, so the product can be exposed as an encryption key.
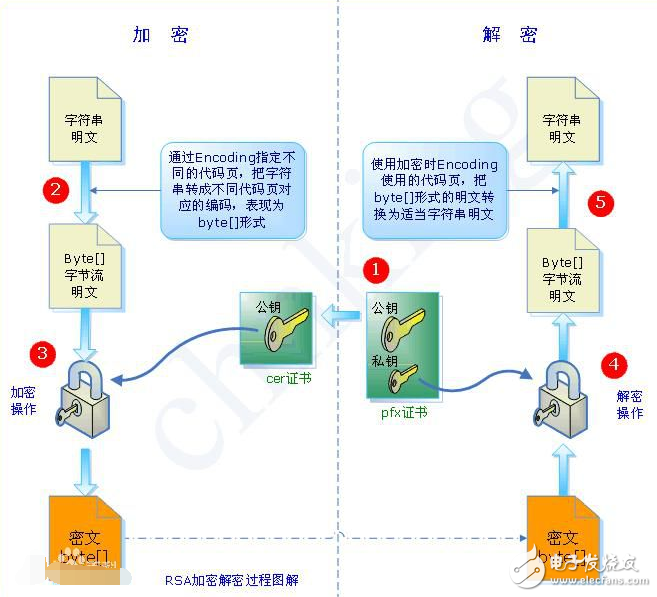
RSA public key cryptosystem. The so-called public key cryptosystem uses different encryption keys and decryption keys, and is a cryptosystem that is " computationally infeasible by deriving a decryption key from a known encryption key."
In the public key cryptosystem, the encryption key (i.e., public key) PK is public information, and the decryption key (i.e., secret key) SK is required to be kept secret. Both the encryption algorithm E and the decryption algorithm D are also public. Although the decryption key SK is determined by the public key PK, the SK cannot be calculated from the PK.
It is based on this theory that the famous RSA algorithm appeared in 1978, which is usually a pair of RSA keys, one of which is a secret key, which is kept by the user; the other is a public key, which can be made public, even Can be registered in the web server. To increase the security strength, the RSA key is at least 500 bits long, and 1024 bits are generally recommended. This makes the amount of encryption computationally large. In order to reduce the amount of calculation, the traditional encryption method is combined with the public key encryption method when transmitting information, that is, the information is encrypted with an improved DES or IDEA session key, and then the session key and information are encrypted using the RSA key. Summary. After the other party receives the information, it decrypts with a different key and can check the message digest.
The RSA algorithm is the first algorithm that can be used for both encryption and digital signatures, and is easy to understand and operate. RSA is the most widely studied public key algorithm. It has been tested by various attacks for more than 30 years from now. It is widely accepted as the best public key solution in 2017. one.
Principle of RSA encryption algorithmIn the RSA encryption algorithm, only a few simple mathematical knowledge such as prime numbers, prime prime numbers, exponential operations, and modular operations are used. Therefore, we also need to understand these concepts.
Prime number
Prime numbers, also known as prime numbers, refer to numbers that cannot be divisible by other natural numbers except for 1 and the integer itself in a natural number greater than one. This concept, we have learned in junior high school, even in elementary school, there is no more explanation here.
Mutual prime number
The explanation on Baidu Encyclopedia is that the two numbers with a common factor of only one are called prime numbers. The explanation on Wikipedia is: mutual quality, also known as mutual quality. If the greatest common factor of N integers is 1, then the N integers are said to be prime.
Common methods for judging the number of prime numbers are as follows:
Two different prime numbers must be prime numbers. For example, 2 and 7, 13 and 19.
One prime number, the other is not a multiple of it, these two numbers are prime numbers. For example, 3 and 10, 5 and 26.
The two adjacent natural numbers are prime numbers. Such as 15 and 16.
The two adjacent odd numbers are prime numbers. Such as 49 and 51.
The larger number is the prime number of the prime number. Such as 97 and 88.
A decimal is a prime number, and a large number is not a multiple of a decimal. Two numbers are prime numbers. For example 7 and 16.
2 and any odd number is a prime number. For example 2 and 87.
1 is not a prime number or a composite number. It is a prime number with any natural number. Such as 1 and 9908.
Twisting and dividing.
Exponential operation
The exponential operation is also called the power calculation, and the calculation result is called the power. Nm means that n is multiplied by m times. The result of considering nm as a power is called "n power of n" or "m power of n". Where n is called the "base" and m is called the "index".
Modular operation
The modulo operation is the remainder operation. "Module" is a transliteration of "Mod". A concept closely related to modular operations is "congruence." Mathematically, when two integers are divided by the same positive integer, if the same remainder is obtained, the two integers are congruent.
Two integers a, b, if they are divided by a positive integer m, the remainder is equal, then a, b is congruent to the modulo m, denoted by: a ≡ b (mod m); read as: a congruence to b mode m, or, a and b are congruent with respect to the modulo m. For example: 26 ≡ 14 (mod 12).
The latest Windows has multiple versions, including Basic, Home, and Ultimate. Windows has developed from a simple GUI to a typical operating system with its own file format and drivers, and has actually become the most user-friendly operating system. Windows has added the Multiple Desktops feature. This function allows users to use multiple desktop environments under the same operating system, that is, users can switch between different desktop environments according to their needs. It can be said that on the tablet platform, the Windows operating system has a good foundation.
Windows Tablet,New Windows Tablet,Tablet Windows
Jingjiang Gisen Technology Co.,Ltd , https://www.gisentech.com