The DES algorithm is a symmetric cryptosystem in the cryptosystem, also known as the US data encryption standard. It is a symmetric cryptosystem encryption algorithm developed by IBM in 1972. The plaintext is grouped by 64 bits, the key length is 64 bits, and the key is actually 56 bits participating in the DES operation (the 8, 16, 24, 32, 40, 48, 56, 64 bits are check digits, so that each key is made The key has an odd number of 1) packetized plaintext group and 56-bit key substitution or exchange method to form a ciphertext group encryption method.
The basic principle of des algorithmThere are three entry parameters: key, data, mode. Key is the key used for encryption and decryption, data is the data encrypted and decrypted, and mode is its working mode. When the mode is the encryption mode, the plaintext is grouped according to 64 bits to form a plaintext group, and the key is used to encrypt the data. When the mode is the decryption mode, the key is used to decrypt the data. In practice, the key only uses 56 of the 64 bits, so that it has high security.
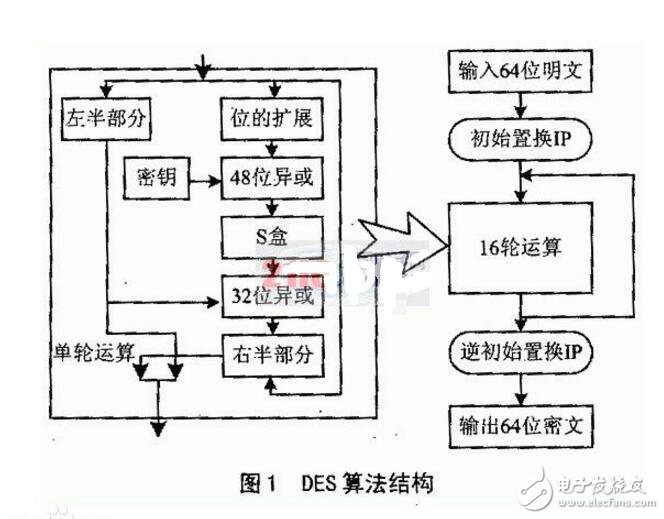
The grouping is short, the key is too short, the password life cycle is short, and the operation speed is slow.
Des algorithm flowThe DES algorithm converts a 64-bit plaintext input block into a 64-bit ciphertext output block. The key used is also 64-bit. The entire algorithm flow chart is as follows:
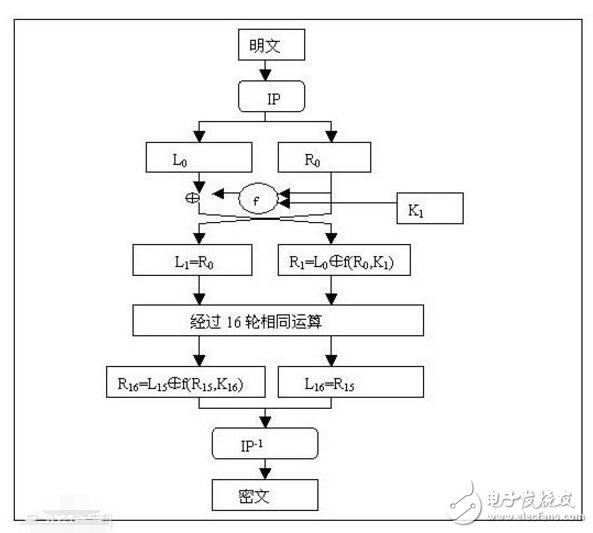
The DES algorithm converts a 64-bit plaintext input block into a 64-bit ciphertext output block. The key used is also 64 bits. Its function is to recombine the input 64-bit data block in bits and divide the output into L0. And R0 two parts, each part is 32 bits long, the replacement rules are as follows:
58,50,12,34,26,18,10,2,60,52,44,36,28,20,12,4,
62,54,46,38,30,22,14,6,64,56,48,40,32,24,16,8,
57,49,41,33,25,17, 9,1,59,51,43,35,27,19,11,3,
61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7,
The 58th place to be entered is changed to the first place, and the 50th place is changed to the second place. . And so on, the last one is the original 7th. L0 and R0 are the two parts after the transposition output. L0 is the left 32 bits of the output, and R0 is the right 32 bits. For example, the input value before the change is set to D1D2D3. . . . . .D64, the result after the initial replacement is: L0=D550. .D8; R0=D57D49. .D7.
After 26 iterations. Obtain L16 and R16, take this as an input, and perform inverse permutation to obtain ciphertext output. The inverse permutation is exactly the inverse of the initial set. For example, after the first bit is subjected to the initial permutation, it is at the 40th position, and by the inverse permutation, the 40th bit is replaced by the first bit. The inverse permutation rule is as follows: Show:
40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31,
38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,
36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,
34,2,42,10,50,18,58 26,33,1,41, 9,49,17,57,25,
Magnification table
32, 1, 2, 3, 4, 5, 4, 5, 6, 7, 8, 9, 8, 9, 10,11,
12,13,12,13,14,15,16,17,16,17,18,19,20,21,20,21,
22,23,24,25,24,25,26,27,28,29,28,29,30,31,32, 1,
Simple transposition table
16,7,20,21,29,12,28,17, 1,15,23,26, 5,18,31,10,
2,8,24,14,32,27, 3, 9,19,13,30, 6,22,11, 4,25,
In the f(Ri, Ki) algorithm description diagram, S1, S2. .S8 is a selection function whose function is to convert 6-bit data into 4-bit data. The function table for the selection function Si (i = 1, 2 . . . . . . . 8) is given below:
Selection function Si
S1:
14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,
0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,
4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,
15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13,
S2:
15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,
3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,
0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,
13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9,
S3:
10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,
13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,
13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,
1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12,
S4:
7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,
13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,
10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,
3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14,
S5:
2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9,
14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,
4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,
11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3,
S6:
12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,
10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8,
9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,
4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13,
S7:
4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,
13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,
1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,
6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12,
S8:
13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,
1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,
7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,
2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11,
Here we use S1 as an example to illustrate its function. We can see that in S1, there are 4 rows of data, named 0, 1, 2, 3 rows; each row has 16 columns, named 0, 1, 2, 3 ,. . . . . . ., 14, 15 columns.
The current input is: D=D1D2D3D4D5D6
Order: column = D2D3D4D5
Line = D1D6
The corresponding number is then found in the S1 table, represented by a 4-bit binary, which is the output of the selection function S1. The generation algorithm of subkey Ki (48bit) is given below.
From the description of the generation algorithm of the subkey Ki, we can see that the initial Key value is 64 bits, but the DES algorithm specifies that the eighth, 16, and . . . . . . The .64 bit is a parity bit and does not participate in the DES operation. Therefore, the actual number of available digits of the Key is only 56. That is, after the transformation of the reduced transposition table 1 is changed, the number of digits of the Key is changed from 64 bits to 56 bits. The 56 bits are divided into two parts, C0 and D0, each of which is 28 bits, and then the first cycle is shifted to the left. Get C1 and D1, combine C1 (28 bits) and D1 (28 bits) to obtain 56 bits, and then select the transposition 2 by narrowing down, so that the key K0 (48 bits) is obtained. And so on, you can get K1, K2. . . . . . ., K15, but it should be noted that the number of left shifts corresponding to the left shift of 16 cycles is based on the following rules:
Cycle left shift number
1,1,2,2,2,2,2,2,1,2,2,2,2,2,2,1
The encryption process of the DES algorithm is described above. The decryption process of the DES algorithm is the same, the only difference is that the sub-key K15 is used in the first iteration, and the second time K14. . . . . . The last time you used K0, the algorithm itself did not change.
The DES algorithm is extremely secure. So far, in addition to attacking the DES algorithm with the exhaustive search method, no more effective methods have been found. The 56-bit long key has an exhaustive space of 256, which means that if the speed of a computer is one million keys per second, it will take nearly 2285 years to search for the full key. It can be seen that this is difficult to achieve. Of course, with the development of science and technology, when ultra-high-speed computers appear, we can consider increasing the length of the DES key to achieve a higher degree of confidentiality.
From the introduction of the above DES algorithm, we can see that only 56 of the 64-bit keys are used in the DES algorithm, and the eighth, 16, and 24, respectively. . . . . . The .64 bit 8 bits are not involved in the DES operation. This brings us an application requirement that the security of DES is based on except 8, 16, 24. . . . . . The change of 256 of the remaining 56 bits outside of .64 is guaranteed. Therefore, in practical applications, we should avoid using 8, 10, 24,. . . . . . The .64 bit is used as a valid data bit, and the other 56 bits are used as valid data bits to ensure that the DES algorithm works safely and reliably. If you don't understand this, put the key Key in 8, 16, 24,. . . . . . .64 bits used as valid data will not guarantee the security of DES encrypted data, and the system will be deciphered by the system that uses DES to achieve confidentiality. This is the misunderstanding of DES algorithm in application, and it is the technician at all levels. Leaders at all levels should be absolutely avoided in the process of use. Today's financial departments and non-financial departments use DES to master the leaders and supervisors of the DES work key Key, which is easy to ignore and seem safe to use. The system has left a great hidden danger of being attacked and being deciphered.
DES algorithm application error data verification data
The author wrote the DES algorithm program with Turbo C, and on the PC, the application error of the above DES algorithm was flawed. The verification data is as follows:
Key: 0x30 0x30 0x30 0x30. . . . . .0x30 (8 bytes)
Data: 0x31 0x31 0x31 0x31. . . . . .0x31 (8 bytes)
Mode: EncrypTIon
Results: 65 5e a6 28 cf 62 58 5f
If the above Key is changed to 8 bytes of 0x31, and Data and Mode are unchanged, the ciphertext obtained after performing DES is exactly the same. Similarly, use Key: 8 0x32 and Key: 8 0x33 to encrypt Data (8 0x31), the graphic output of the two is the same: 5e c3 ac e9 53 71 3b ba
We can get a conclusion:
Key is 0x30 and is the same as 0x31;
Key is 0x32 and is the same as 0x33. . . . . . .
When the Key is changed from 8 0x32 to 8 0x31, it looks like a new Key, but since 0x30 and 0x31 are only at 8, 16, 24. . . . . .64 has changed, and the DES algorithm does not use Key's 8, 16, . . . . . . The .64 bit is the valid data bit of the Key, so the result of the encryption is the same.
Verification data for DES decryption:
Key: 0x31 0x31. . . . . .0x31 (8 0x31)
Data: 65 5e a6 28 cf 62 58 5f
Mode: DecrypTIon
Result: 0x31 0x31. . . . . .0x31 (8 0x31)
It can be seen from the above that both the DES algorithm encryption and decryption work correctly. The only thing to avoid is: in the application, avoid the 8th, 16th. . . . . The .64 bit is used as a valid data bit, thus avoiding the misunderstanding of the DES algorithm in the application.
Avoid the specific operation of DES algorithm application misunderstanding
In the process of using, managing, and replacing the DES key Key, the application misunderstanding of the DES algorithm should be absolutely avoided, that is, the 8th, 16th, and 24th of the Key must not be used. . . . . The .64 bit is used as a valid data bit to manage the Key. This point is especially recommended to leaders and decision makers in the financial banking and non-financial industries, especially those responsible for managing keys, and this point is highly valued. Some bank financial transaction networks use the method of periodically changing the DES key Key to further improve the security and reliability of the system. If the above application misunderstanding is neglected, then replacing the new key will be futile, for the financial transaction network. Safe operation will be very dangerous, so the replacement key must ensure that the new Key is really different from the old Key, except for the 8, 16, 24. . Other bits of .64 bits have changed, so be sure to pay attention to it!
/*****************************************The following is the verification using the DES encryption tool result************************************************* ***/

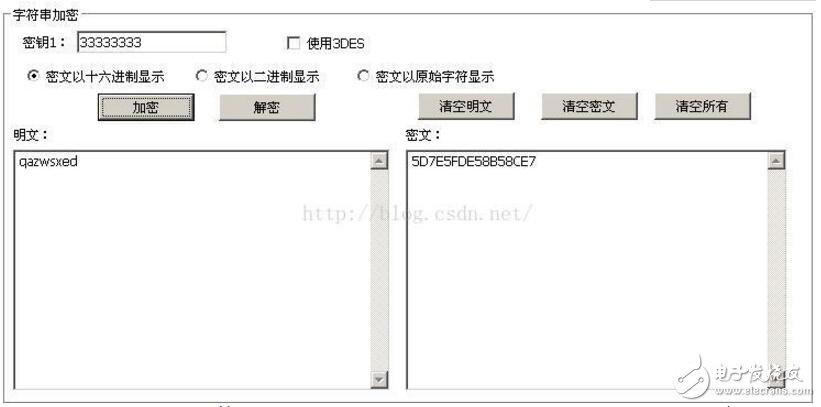
The above two figures only change the 8th, 16th, 24th, 36th, 48th, 56th and 64th bits in the key, verifying that the encrypted ciphertext is the same!
Switching Current Transformer,Outdoor Switching Current Transformer,Busbar Built-In Current Transformer,Outdoor Split Core Current Transformer
Zibo Tongyue Electronics Co., Ltd , https://www.tongyueelectron.com