1. Overview of wireless sensor network transmission protocols
1. Composition of wireless sensor network protocol stack
The wireless sensor network protocol stack is composed of five parts: physical layer, data link layer, network layer, transport layer, and application layer, and corresponds to the five-layer protocol of the Internet protocol stack.
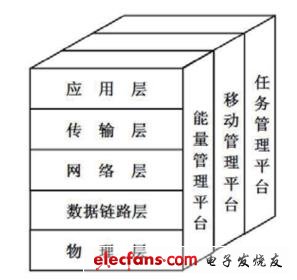
Wireless sensor network protocol stack
Physical layer: data collection, sampling, sending, receiving, and signal modulation and demodulation;
Data link layer: media access control, establishment of reliable communication links between network nodes, providing reliable communication channels for neighbor nodes;
Network layer: discover and maintain routes;
Application layer: Provide security support to implement key management and secure multicast;
Transport layer: Provide reliable transmission, flow control, error control, QoS and other services for end-to-end connections. Even in the OSI model, only this layer is responsible for overall data transmission and control, so it is very important.
2. The shortcomings of traditional agreements
Traditional IP networks mainly use the UDP and TCP protocols of the transport layer in the protocol stack to control data transmission. The UDP protocol is a connectionless transmission protocol that does not provide flow control and error recovery of data packets; the TCP protocol provides reliable transmission guarantees, such as sliding window and AIMD mechanisms for congestion control, and retransmission for errors control. But the TCP protocol cannot be directly used for WSN, the main reasons are as follows:
(1) The TCP protocol follows the end-to-end design idea. The transmission control task of the data packet is given to the end node of the network, and the intermediate node only undertakes the forwarding of the data packet. While WSN is data-centric, intermediate nodes may perform in-network processing on the relevant data, that is, comprehensively process the information in multiple data packets according to the data correlation, and obtain new data packets to send to the receiver At the end, directly using the TCP protocol will cause this to be regarded as a packet loss and cause a retransmission.

(2) The TCP handshake mechanism for establishing and releasing connections is relatively complicated and takes a long time, which is not conducive to the sensor nodes' timely feedback of relevant information of the monitored objects. The dynamic change of WSN network topology also brings certain difficulties to the establishment and maintenance of TCP connection status.
(3) The TCP protocol uses a packet-based reliability metric, that is, to make every effort to ensure that all sent data packets are correctly received by the receiving node. In WSN, there may be multiple sensor nodes monitoring the same object, which makes the monitoring data have strong redundancy and correlation. As long as the monitoring information finally obtained can describe the real state of the object, it has a certain fidelity, and does not necessarily require the complete reliability of the data packet transmission. This method is also called event-based reliability. measure.
(4) The retransmission of data packets in the TCP protocol is guaranteed by the ACK feedback and timeout mechanism between the end nodes. The amount of data contained in the sensor network data packet is relatively small, and the transmission of a large number of ACK packets will increase the transmission load and energy consumption. In addition, every time the ACK is acknowledged and the data packet is retransmitted, the multi-hop transmission path is sent from the sending end to the destination end, causing energy consumption of all nodes along the entire path.
(5) Out-of-sequence data packet transmission caused by non-congested packet loss and multiplexing in WSN will cause an error response of the TCP protocol, causing the sending end to frequently enter the congestion control stage, resulting in reduced transmission performance.
(6) The TCP protocol requires that each network node has a unique or independent network address for the entire network. In large-scale WSN, in order to reduce the transmission consumption caused by long address bits, the sensor node may only have a local independent or geographically related network address or use a network address-free transmission scheme, and cannot directly use the TCP protocol.
3. Research progress of WSN transmission protocol
The current research work on wireless sensor network transmission protocol still focuses on congestion control and reliable guarantee. The study divides congestion control into flow control, demultiplexing, data aggregation, and virtual gateways; reliable guarantees include data retransmission and redundant transmission.
In flow control, the ERST, PORT and IFRC protocols are congestion control protocols based on report rate adjustment; Fusion and CCF are congestion control protocols based on forward rate adjustment, suitable for networks that require high data fidelity; Buffer-based, PCCP, CODA It is a congestion control protocol based on integrated rate adjustment. ERST considers the factors of reliability and energy consumption, and reduces the congestion by adjusting the report rate; the PORT protocol models the report rate adjustment problem as an optimization problem to solve the shortcomings of ERST; IFRC focuses on ensuring that the channel bandwidth can be more fairly Shared by multiple neighbors.
Fusion uses a token bucket mechanism. Nodes accumulate tokens according to certain rules and consume one token when sending data once. CCF uses a rate comparison method. When congestion occurs, the node compares its own forwarding rate with the forwarding rate notified by the parent node. To forward the packet with the smaller value.
Buffer-based adopts a lightweight control mechanism based on buffer. Before sending a data packet, the node is required to monitor whether the buffer overflow of the neighbor node; PCCP assigns different weighted priorities to the data flow to ensure the adjustment fairness; CODA combines open-loop and closed-loop control methods to solve congestion. Open network control is enabled when network traffic bursts cause local congestion. At the same time, if the frequency of a monitored event is lower than the set channel throughput, the source node can adjust the reporting rate by itself, otherwise it starts closed-loop congestion control.
Multi-path distribution is to disperse traffic through multi-path forwarding to solve the congestion problem. Among them, the ARC protocol is to use redundant nodes in the network to build a new forwarding path. CAR is similar to the ARC method, and BGR is to increase the direction deviation range in geographic routing to expand the optional range of the forwarding path.
The necessity and importance of data aggregation (melting) have been described above. The agreement includes CONCERT and PREI. The former uses adaptive aggregation, while the latter divides the network into networks of the same size and aggregates data from the same grid.
In terms of reliability, the data retransmission protocol includes three types: gateway-to-node, node-to-gateway, and two-way reliable guarantee; redundant transmission includes copy transmission (AFS, Rein form, MMSPEED, GRAB) and coding redundancy.
PSFQ and GARUDA are gateway-to-node. The former uses delayed cache to control, while the latter establishes a hierarchical structure and performs periodic packet loss recovery. RMST and RBC are from the node to the gateway. The former is designed based on a single routing protocol. In addition to the original direction from the data source to the gateway, a backward path is added for feedback of packet loss. BRTM is a two-way reliable guarantee.
In addition, there are 5 kinds of random delivery transmission protocols and they are modeled and analyzed separately, and related conclusions are made on the basis of simulation comparison. These agreements include:
1) Hop-by-hop reliable transmission protocol HHR, hop-by-hop reliable transmission protocol with response
HHRA The latter is a variant of the former. HHR is the simplest such protocol. In the protocol, a forwarding node sends the same data packet to its next hop sending node multiple times. As long as the next hop node receives a copy of the retransmitted data packet, it will continue to send. HHRA requires the forwarding node to wait for the response packet from the receiver. If a response packet is received, the forwarding of subsequent copies of this hop is terminated.
2) Hop-by-hop broadcast transmission protocol HHB, hop-by-hop broadcast transmission protocol with response
HHBA The latter is a variant of the former. In HHB, the forwarding node sends the same data packet to its multiple next-hop neighbors multiple times. If any neighbor node successfully receives at least one data packet, it continues to forward the packet with a certain probability. HHBA introduces a response mechanism to increase transmission reliability and reduce energy consumption during transmission.
3) Rein form agreement
The protocol simultaneously sends multiple copies of a data packet on multiple random paths to generate data redundancy and improve transmission reliability
4) Collaborative transmission protocol based on clustering. The improvement of transmission efficiency and network throughput is analyzed. The protocol is divided into four steps: 1) clustering, which is to determine the cluster head and determine the nodes for cooperative transmission in each cluster; 2) information transmission within the cluster; 3) the cooperative node in the cluster sends data to the sink node; 4) the sink node receives And heartbeat. The main problem of this protocol is the synchronization between coordinated nodes. Researchers believe that this technology can be used in a variety of occasions such as wireless ad hoc networks, wireless local area networks and wireless sensor networks
5) Real-time transmission protocol. Mainly studied the SPEED protocol, and conducted experiments on the platform built by TInyOS1.1.11 and the Micaz node of Crossbow.
to sum up:
The transmission control protocol of WSN needs further study in the following aspects:
1) Design a transmission control protocol for cross-layer collaboration. The transmission control task in WSN cannot be completed solely by the transmission layer. Each layer in the sensor node protocol stack should fully interact and cooperate under the coordination of the transmission layer control mechanism to jointly support and ensure the reliable transmission of data.
2) Improve the comprehensive control capability of the transmission control protocol. In the WSN application process, congestion and packet loss in the network may occur at the same time and affect each other, and data exchange between the gateway and the node will also occur frequently. Most of the current control protocols only deal with a problem (congestion or packet loss) in the direction of a single data flow. The new transmission control protocol should provide a comprehensive comprehensive control mechanism.
3) Control strategy based on multiple priorities. Different data streams appearing on the network may have different requirements on reliability, and it is necessary to consider the handling of priority issues when designing the protocol.
4) The transmission control protocol needs to provide fairness guarantee. While ensuring transmission efficiency, multiple data streams in the network should share wireless channels for data transmission according to the pre-defined fairness principle.
5) Support data-centric design in WSN. WSN's data-centric features have brought some new design solutions, such as node design without independent addresses, data processing on the network and clustered network structure. The new transmission control protocol needs to provide support for these solutions.
6) Provide support for node mobility. At present, WSN transmission control protocols basically assume that sensor nodes and networks are static. However, in battlefield, logistics and other applications, the movement of nodes will bring more unreliable factors to the network transmission, and increase the occurrence of packet loss. It is necessary to design a control protocol with higher processing efficiency and faster processing speed.
Surround Speakers,Home Theater Systems,Wooden Cabinet Speakers,Commercial Conference Speaker Systems
The ASI Audio Technology Co., Ltd , https://www.asi-sound.com